VPN IPSec (site-to-site) between Mikrotik virtual routers behind NAT Traversal (NAT-T)¶
Description
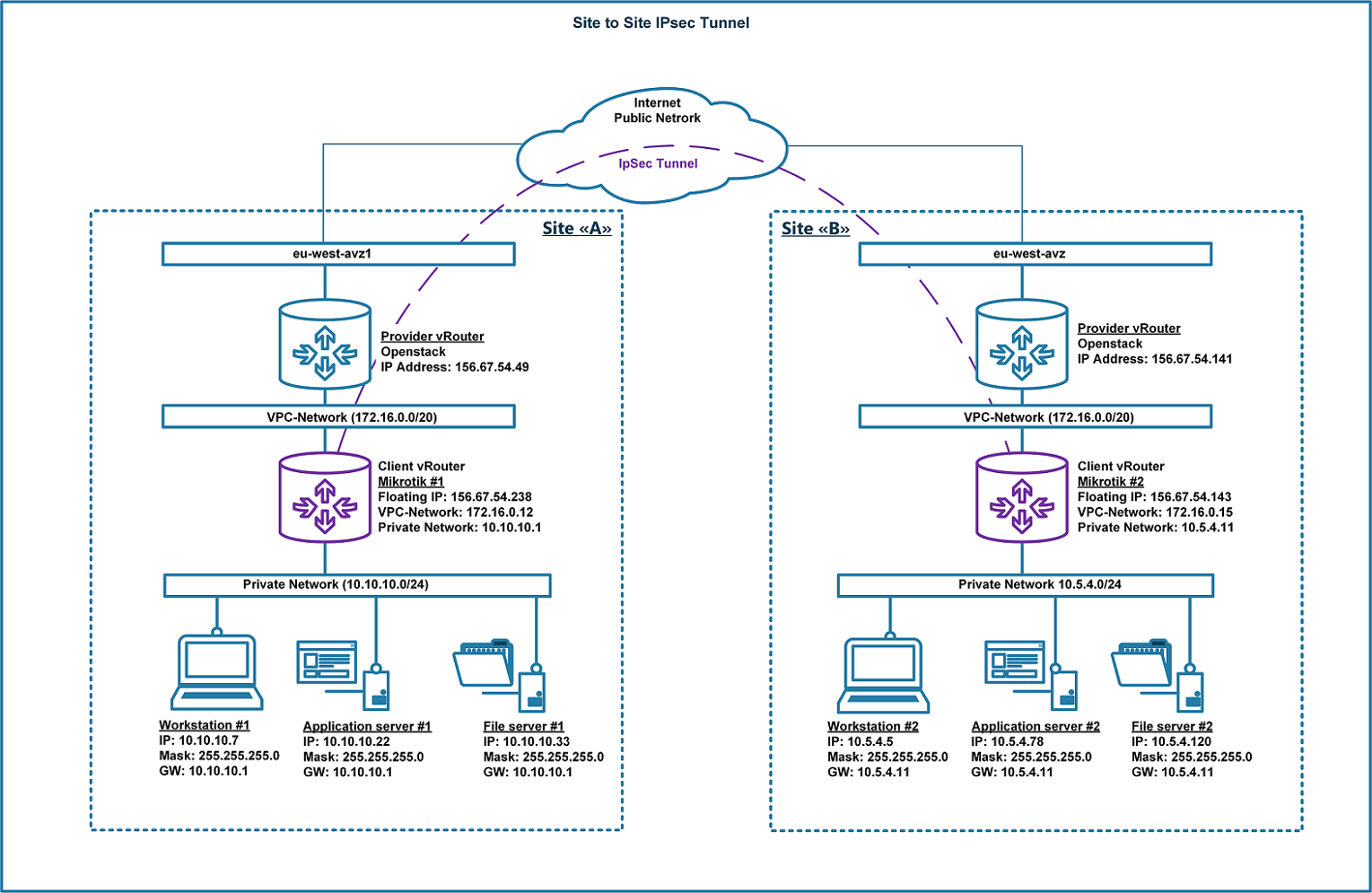
Consider the structure of the VPN ‘site-to-site’ connection as shown below. Two remote Mikrotik virtual routers are connected to the public Internet network through a temporary network node - the router of the provider. By this means, both Mikrotik routers are situated behind the NAT-T. The article contains examples of the configuration of equipment via the console and also through the winbox management interface (GUI).
Initial conditions
The workstations and also the existing infrastructure are also behind the NAT. Each of sites A and B have their own private subnetwork:
- 10.10.10.0/24 for Site “A”
- 10.5.4.0/24 for Site “B”
- Version for Mikrotik routers: RouterOS 6.41.2 stable (CHR).
- Version for WinBox: 3.18.
Warning
Depending on the OS version of the router or software, subsequent configuring may vary.
Note
To set up a VPN connection, the following required conditions must be satisfied:
Network availability between routers:
- Protocol: UDP, port 500 (for IKE, to manage encryption keys).
- Protocol: UDP, port 4500 (for IPSEC NAT-Traversal mode).
- Protocol: ESP, value 50 (for IPSEC).
- Protocol: AH, value 51 (for IPSEC).
The firewall rules must not block network traffic between the routers and the private subnetworks.
Private subnetworks that will be connected by means of IPSec must be different and must not include each other.
| Client vRouter | Floating IP | VPC-Network IP | Private Network IP |
| Site “A” Mikrotik #1 | 156.67.54.238/32 | 172.16.0.12/32 | 10.10.10.1/32 |
| Site “B” Mikrotik #2 | 156.67.54.143/32 | 172.16.0.15/32 | 10.5.4.11/32 |
In this example the initial configuring of the secure IPSec site-to-site VPN connection is performed, thereby connecting the private networks 10.10.10.0/24 and 10.5.4.0/24, which are behind the routers.
Site A configuration
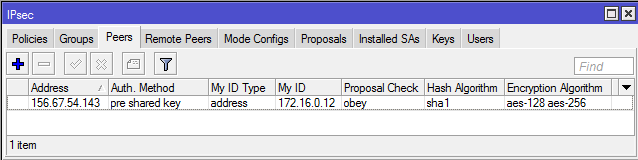
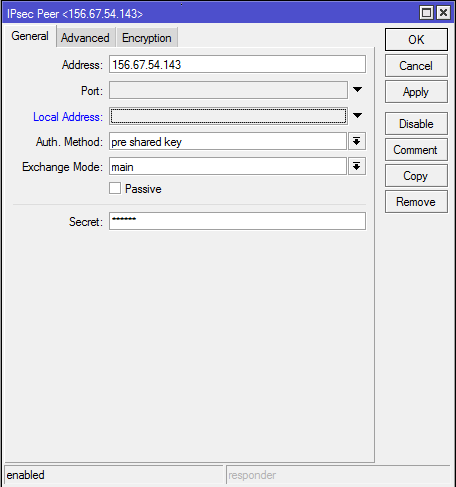
1-A. Configuring IPsec peer. In this step the following parameters must be set:
- address (of remote peer router),
- auth-method (authentication method),
- secret (secret word),
- my-id (my identifier).
The remaining parameters are left at their default values, without changes. This configuration is performed below from the console:
/ip ipsec peer
add address=156.67.54.143/32 my-id=address:172.16.0.12 auth-method=pre-shared-key secret="123456"
Check the changes that have been made:
[admin@Site "A"] > ip ipsec peer print
Flags: X - disabled, D - dynamic, R - responder
0 address=156.67.54.143/32 auth-method=pre-shared-key secret="123456" generate-policy=no policy-template-group=default exchange-mode=main
send-initial-contact=yes nat-traversal=yes my-id=address:172.16.0.12 proposal-check=obey hash-algorithm=sha1
enc-algorithm=aes-256,aes-128 dh-group=modp1024 lifetime=1d dpd-interval=2m dpd-maximum-failures=5
As can be seen from the output of the command ‘ip ipsec peer print’, the parameters have been applied correctly. Now consider how the same configuration is made using the management interface of the router:
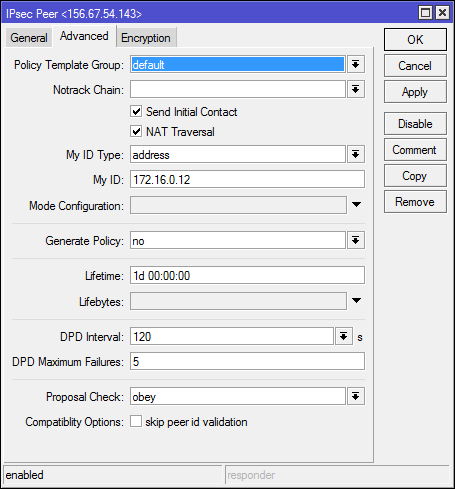
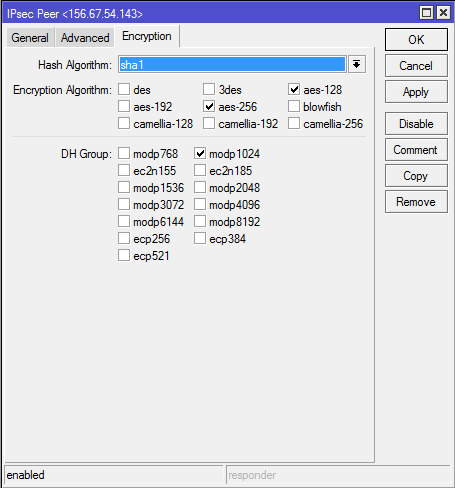
2-A. For the following steps it is important that the authentication and encryption algorithms provided coincide in both routers. In this example the default settings of the parameters are used. To view and check the settings of the proposal parameter, execute the command ‘ip ipsec proposal print’:
[admin@Site "A"] > ip ipsec proposal print
Flags: X - disabled, * - default
0 * name="default" auth-algorithms=sha1
enc-algorithms=aes-256-cbc,aes-192-cbc,aes-128-cbc lifetime=30m
pfs-group=modp1024
3-A. Set the policy for IPSec:
/ip ipsec policy
add src-address=10.10.10.0/24 src-port=any dst-address=10.5.4.0/24 dst-port=any \
sa-src-address=172.16.0.12 sa-dst-address=156.67.54.143 \
tunnel=yes action=encrypt proposal=default
Check the changes that have been made to the policy parameters:
[admin@Site "A"] > ip ipsec policy print
Flags: T - template, X - disabled, D - dynamic, I - invalid, A - active, * - default
0 T * group=default src-address=::/0 dst-address=::/0 protocol=all proposal=default template=yes
1 A src-address=10.10.10.0/24 src-port=any dst-address=10.5.4.0/24 dst-port=any protocol=all
action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=172.16.0.12
sa-dst-address=156.67.54.143 proposal=default ph2-count=1
As can be seen from the output of the command ‘ip ipsec policy print’, the parameters have been applied correctly. Now consider how the same configuration is made using the management interface of the router:
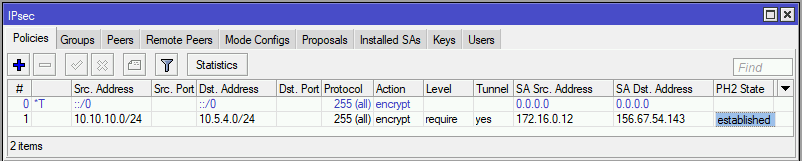
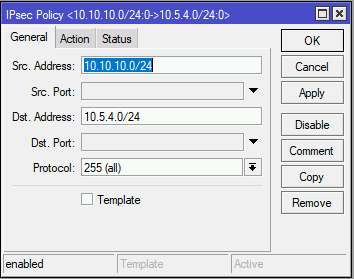
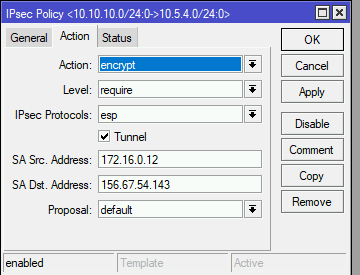
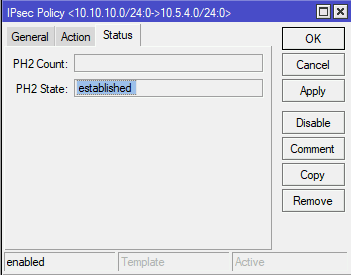
Having completed the 3 steps above for configuring the router at site A, we can begin configuring the router for site B.
Site B configuration
1-B. Configuration of the ‘IPsec peer’ parameters for site B is almost identical to that for site A, with differences for only two parameters: the IP address of the remote peer (address), and its identifier (my-id)’.
Performing the configuration from the console:
/ip ipsec peer
add address=156.67.54.238/32 my-id=address:172.16.0.15 auth-method=pre-shared-key secret="123456"
Check the changes that have been made:
[admin@Site "B"] > ip ipsec peer print
Flags: X - disabled, D - dynamic, R - responder
0 address=156.67.54.238/32 auth-method=pre-shared-key secret="123456" generate-policy=no
policy-template-group=default exchange-mode=main send-initial-contact=yes nat-traversal=yes
my-id=address:172.16.0.15 proposal-check=obey hash-algorithm=sha1 enc-algorithm=aes-256,aes-128
dh-group=modp1024 lifetime=1d dpd-interval=2m dpd-maximum-failures=5
As can be seen from the output of the command ‘ip ipsec peer print’, the parameters have been applied correctly. Now consider how the same configuration is made using the management interface of the router:
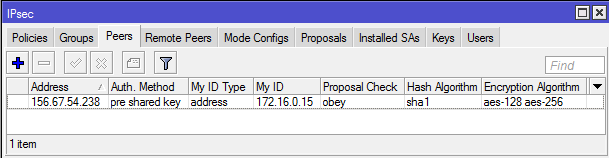
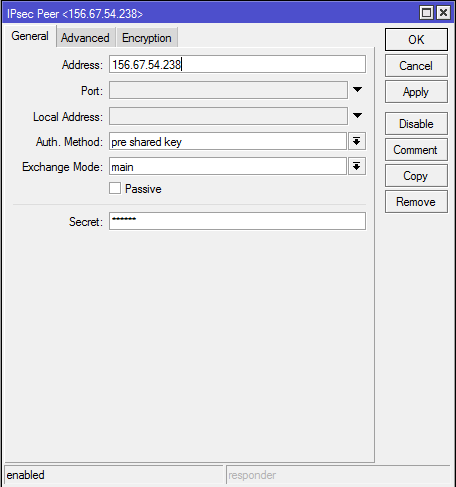
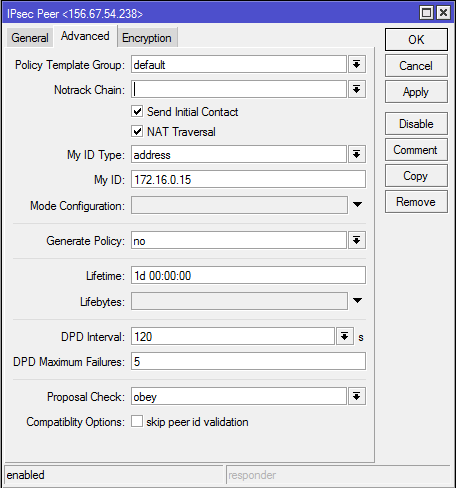
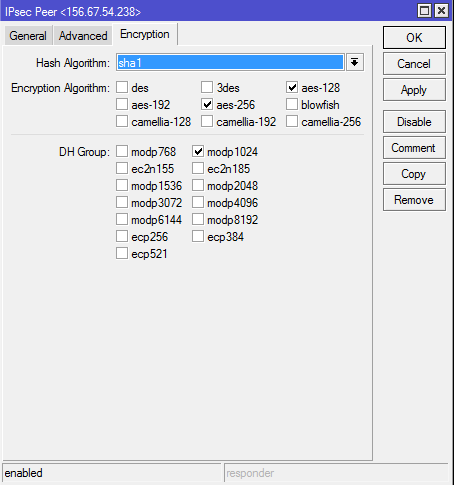
2-B.Check that the proposal parameters have been created by default and match the router parameters for site A:
[admin@Site "B"] > ip ipsec proposal print
Flags: X - disabled, * - default
0 * name="default" auth-algorithms=sha1 enc-algorithms=aes-256-cbc,aes-192-cbc,aes-128-cbc lifetime=30m
pfs-group=modp1024
The results of the output of the ‘ip ipsec proposal print’ command are the same on both routers and a tunnel is created between them.
3-B. Create an IPsec policy at site B:
/ip ipsec policy
add src-address=10.1.101.0/24 src-port=any dst-address=10.1.202.0/24 dst-port=any \
sa-src-address=192.168.80.1 sa-dst-address=192.168.90.1 \
tunnel=yes action=encrypt proposal=default
Check the changes that have been made to the policy parameters:
[admin@Site "B"] > ip ipsec policy print
Flags: T - template, X - disabled, D - dynamic, I - invalid, A - active, * - default
0 T * group=default src-address=::/0 dst-address=::/0 protocol=all proposal=default template=yes
1 A src-address=10.5.4.0/24 src-port=any dst-address=10.10.10.0/24 dst-port=any protocol=all
action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=172.16.0.15
sa-dst-address=156.67.54.238 proposal=default ph2-count=1
As can be seen from the output of the command ‘ip ipsec policy print’, the parameters have been applied correctly. Now consider how the same configuration is made using the management interface of the router:
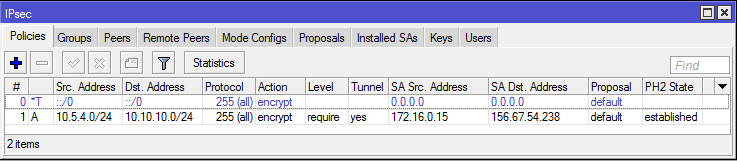
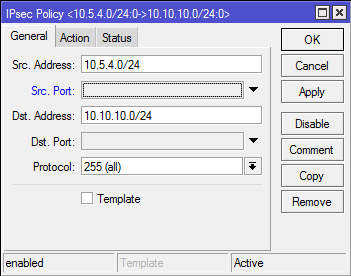
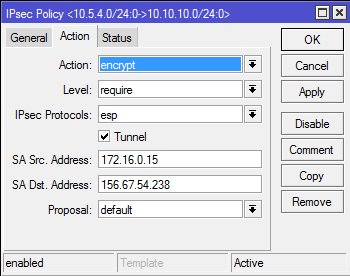
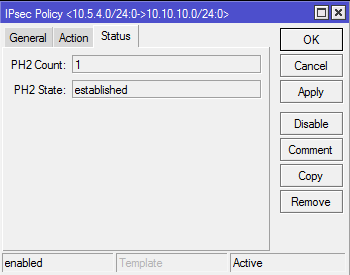
When steps 1-A-3-A and 1-B-3-B have been correctly completed, the tunnel should be established and two security associations should be created on both routers.
To check that the VPN connection has been established on both routers it is necessary to perform the commands ‘ip ipsec remote-peers print’ and ‘ip ipsec installed-sa print’ in sequence.
[admin@Site "A"] > ip ipsec remote-peers print
Flags: R - responder, N - natt-peer
# ID STATE REMOTE-ADDRESS DYNAMIC-ADDRESS UPTIME
0 RN established 156.67.54.143 7h55m41s
[admin@Site "B"] > ip ipsec remote-peers print
Flags: R - responder, N - natt-peer
# ID STATE REMOTE-ADDRESS DYNAMIC-ADDRESS UPTIME
0 N established 156.67.54.238 7h58m45s
It can be seen from the result of executing the command ‘ip ipsec remote-peers print’ that the connection has been established (STATE - established). The flag ‘N’ indicates here that the remote peer is situated behind the NAT.
[admin@Site "A"] > ip ipsec installed-sa print
Flags: H - hw-aead, A - AH, E - ESP
0 E spi=0xBDAD9B src-address=156.67.54.143:4500 dst-address=172.16.0.12:4500 state=mature auth-algorithm=sha1
enc-algorithm=aes-cbc enc-key-size=256 auth-key="b09b24558822f70d618f86479ff06c948da2c3d8"
enc-key="9d41abb6e038fead6b2943251e9a18589cbf96a1b21c9424d62c0d26d8cf3d08" add-lifetime=24m/30m
replay=128
1 E spi=0xE4C9D3 src-address=172.16.0.12:4500 dst-address=156.67.54.143:4500 state=mature auth-algorithm=sha1
enc-algorithm=aes-cbc enc-key-size=256 auth-key="55971cf3d89e5377d1191ed7f9ba4253f1b6fe05"
enc-key="0415a2ad4d141fd10642bf3c8e99f24e2d424295ac2b0f84d10c351972359706" add-lifetime=24m/30m
replay=128
[admin@Site "B"] > ip ipsec installed-sa print
Flags: H - hw-aead, A - AH, E - ESP
0 E spi=0xE4C9D3 src-address=156.67.54.238:4500 dst-address=172.16.0.15:
state=mature auth-algorithm=sha1 enc-algorithm=aes-cbc enc-key-size=
auth-key="55971cf3d89e5377d1191ed7f9ba4253f1b6fe05"
enc-key="0415a2ad4d141fd10642bf3c8e99f24e2d424295ac2b0f84d10c3519723
add-lifetime=24m/30m replay=128
1 E spi=0xBDAD9B src-address=172.16.0.15:4500 dst-address=156.67.54.238:
state=mature auth-algorithm=sha1 enc-algorithm=aes-cbc enc-key-size=
auth-key="b09b24558822f70d618f86479ff06c948da2c3d8"
enc-key="9d41abb6e038fead6b2943251e9a18589cbf96a1b21c9424d62c0d26d8c
add-lifetime=24m/30m replay=128
Rules for ‘bypassing’ NAT
At this stage, if traffic is sent via the IPsec tunnel, it will not work; the packets will be lost. This is because both routers have the NAT masquerading rules, which change the source address before the packet is encrypted. The router cannot encrypt the packet since the source address does not correspond to the address specified in the policy configuration. For further information on this, see Example protocol for IPsec packets..
To rectify this situation it is necessary to create a NAT bypass rule.
Site A router
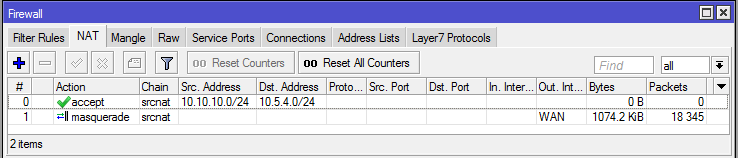
/ip firewall nat
add chain=srcnat action=accept place-before=0 \
src-address=10.10.10.0/24 dst-address=10.5.4.0/24
[admin@Site "A"] > ip firewall nat print
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat action=accept src-address=10.10.10.0/24 dst-address=10.5.4.0/24 log=no log-prefix=""
1 chain=srcnat action=masquerade out-interface=WAN log=no log-prefix=""
Site B router
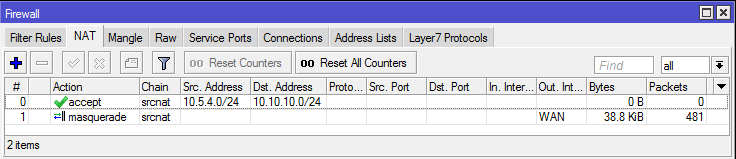
/ip firewall nat
add chain=srcnat action=accept place-before=0 \
src-address=10.5.4.0/24 dst-address=10.10.10.0/24
[admin@Site "B"] > ip firewall nat print
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat action=accept src-address=10.5.4.0/24 dst-address=10.10.10.0/24 log=no log-prefix=""
1 chain=srcnat action=masquerade out-interface=WAN log=no log-prefix=""
Note
If you attempted to establish an IP connection before the NAT bypass rule was added, you must clear the connection table of any existing connections or restart both routers.
It is vital that the bypass rule be above all the other NAT rules.