Security¶
The security of the cloud and the information contained in it is ensured on a number of levels.
Level 1

All SIM-Networks equipment is located in two data centres, Tier III and Tier III+ respectively, in the city of Karlsruhe, Germany’s IT capital. Both data centres are certified in accordance with the European standard ISO 27001 for the security, construction and management of data centres, and are periodically re-certified. This guarantees the physical isolation of everything that is situated or occurs in the data centre from the outside world. Authorised and allocated access to the premises and the buildings is constantly controlled by appropriate regulations and systems.
Level 2

The entire SIM-Cloud infrastructure and software have been designed, installed and set up in such a way that it can be accessed solely by SIM-Networks technicians. All cloud-based systems and services interact in protected and isolated environments and networks; all connections employ encryption and strong authentication. All SIM-Cloud elements are monitored constantly (24/7) by automated monitoring systems and an group of engineers.
Level 3

The Federal Republic of Germany has an exemplary system of justice with strong legislation in place to protect private property. This guarantees that no spontaneous seizure or removal of equipment is possible.
ISOLATION OF CLIENTS IN THE CLOUD
Each user of the public cloud is assigned access to a precisely described limit of virtual resources (vCPU, vRAM, vHDD) appropriate to their objectives. The possibility of exceeding this limit is prevented by technical means. Users are not visible to one another and there does not exist any situation in which unconnected clients can ‘bump into’ each other in the virtual environment.
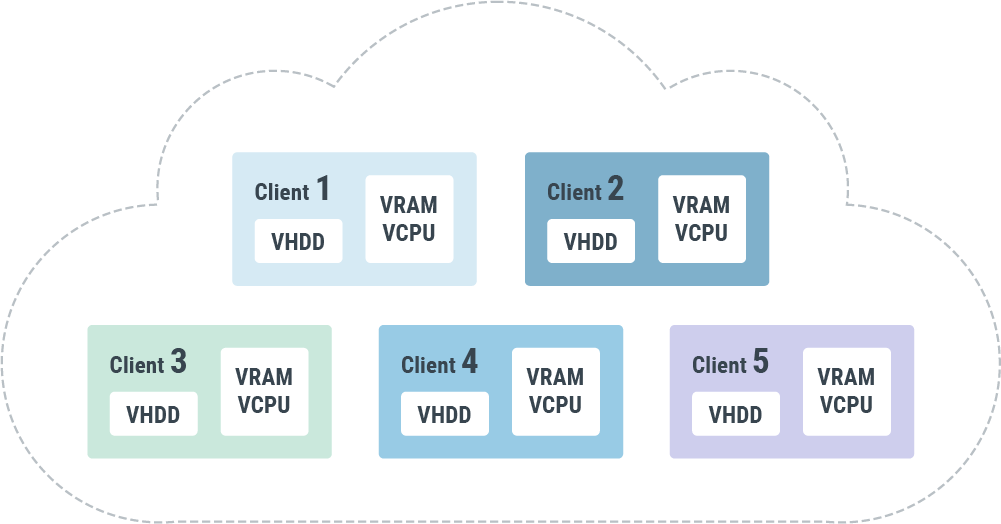
The isolation of data and applications operating within virtual machines is created by the KVM hypervisor. Network traffic of the client within private networks is protected by VXLAN technologies, which wholly prevent access from one isolated network to another. Thanks to these technologies, all data and private traffic of each client are isolated from those of others. You may also, at your discretion, use additional encryption techniques for data and network traffic, over and above the technologies offered by us.